场景简介
在 Web 或 App 开发过程中,用户的认证和权限处理是非常重要的一个模块,这里包括用户注册、登录认证及管理对应的权限。除了用户名密码登录外,通过第三方社交帐号登录也是非常重要的需求,在国外主要是 Google、Facebook 或 Apple 登录等,而在国内则主要是微信、微博登录等。
身份认证与授权实现起来相应复杂,因此在 AWS 云上提供了 Cognito 服务,以帮助开发者更快、更安全地接入用户注册/登录和访问控制功能。Cognito 服务让企业可以把更多的精力花在核心业务上,去关注创新、创收,而非过多关注身份认证与授权相关的底层技术细节。
Authing 的价值
AWS Cognito User Pool 服务在国内区域暂时未上线,对于想要在中国使用 Cognito 这类 IDaaS 服务的企业来说,Authing 将是更好的选择。Authing 可以解决使用 Cognito 的诸多问题,使用 Authing User Pool,可以替代 Cognito User Pool,构建起国内用户与 AWS 资源之间的桥梁。
架构设计
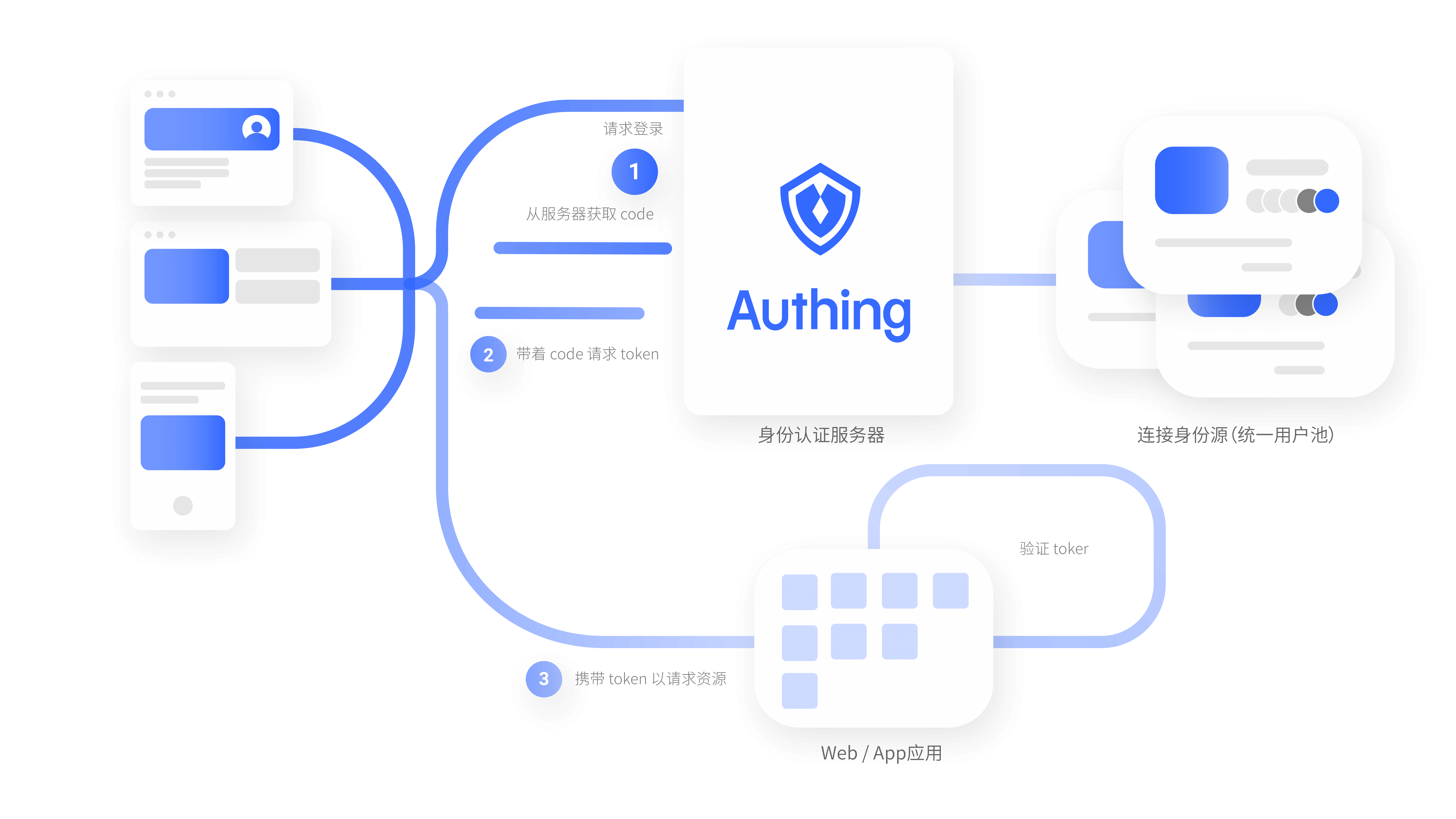
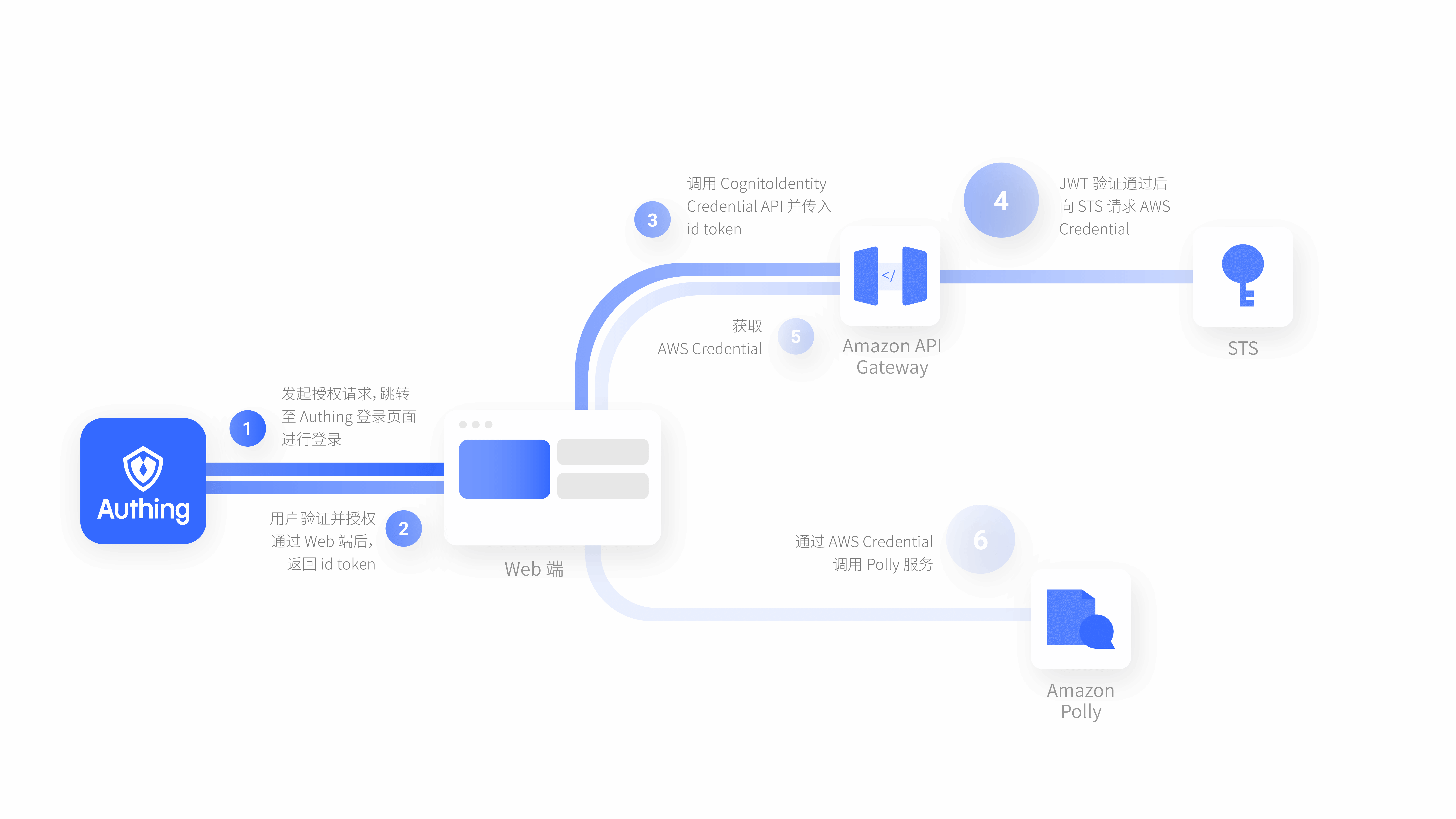
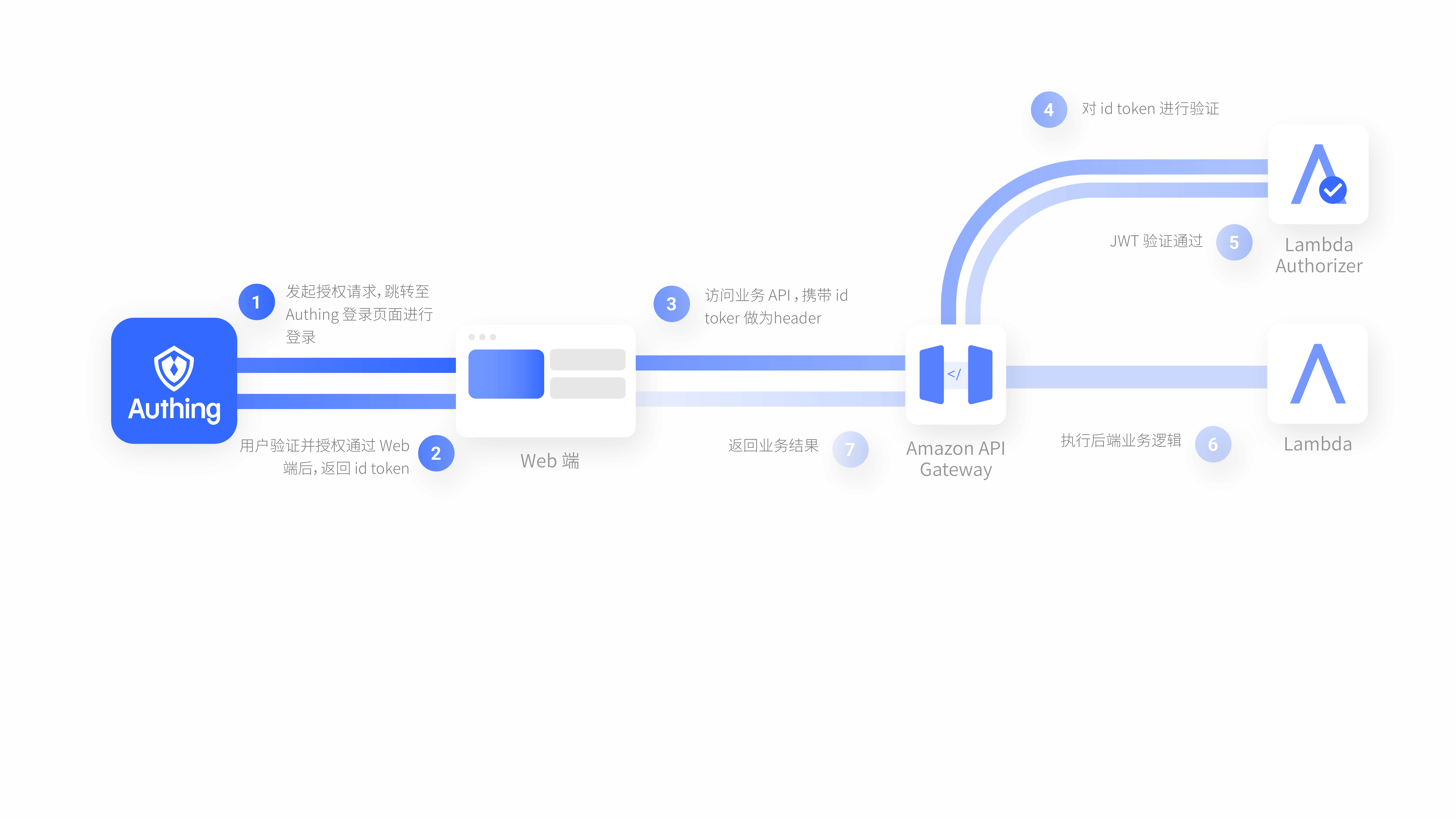
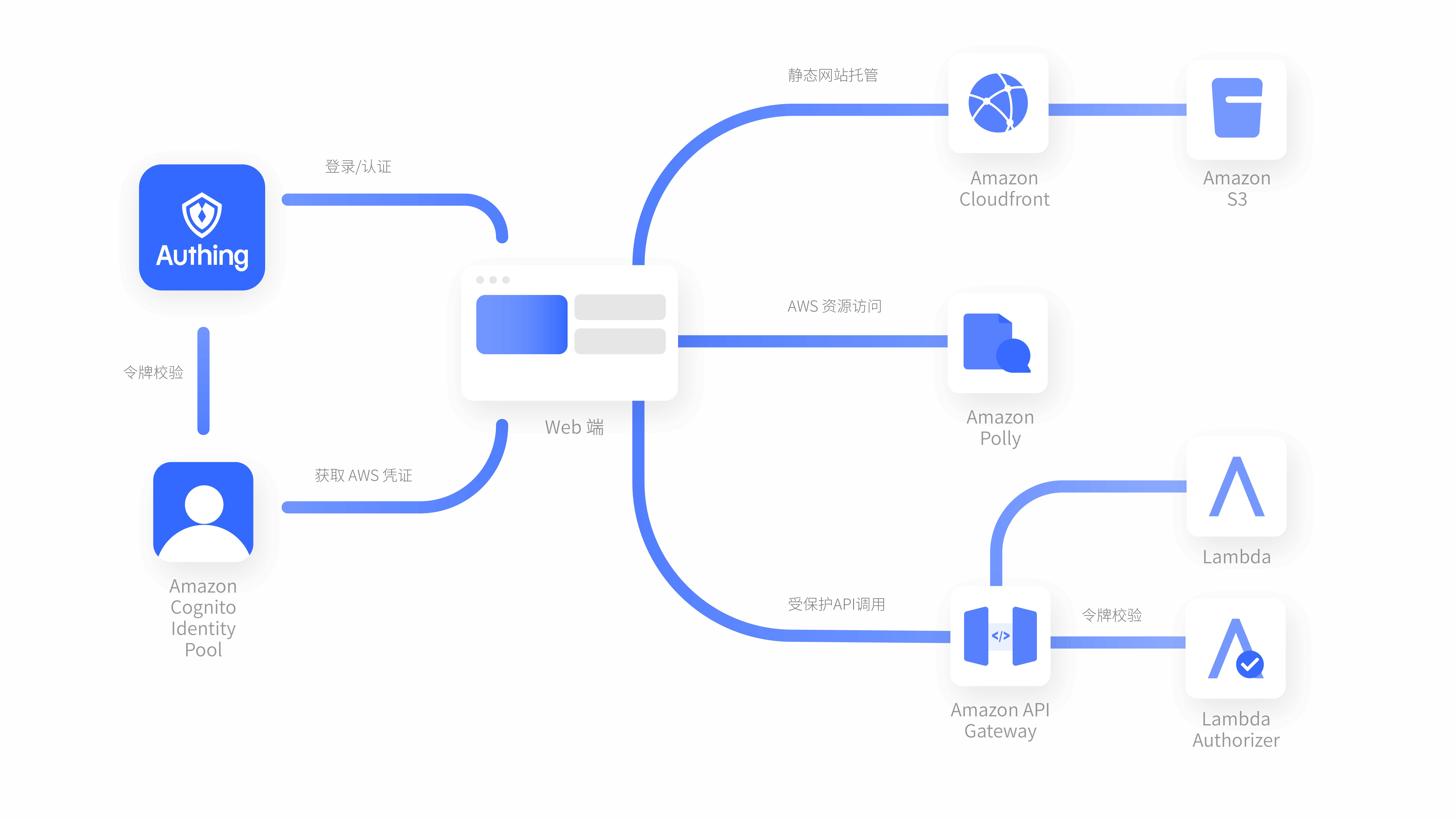
演示网站整体架构
通过 S3 进行静态网站托管, 并利用 Cloudfront 进行静态内容加速和 HTTPS 证书挂载。
通过 Authing 进行登录认证并获取令牌,作为 User Pool 的替代方案。
访问 API Gateway 提供的 REST API。
通过 Cognito Identity Pool 获取临时 AWS 凭证,访问 AWS 资源(这里以 Polly 服务为例)。
Authing 如何支持各种场景
API 安全
在零信任环境中提高 API 安全性并确保内部和外部合作伙伴用例的合规性可能非常具有挑战性。Authing 基于开放标准的方法提供端到端的 API 安全和管理。
对于用户
通过支持所有 OAuth 2.0 授权流以及细粒度的范围和权限,轻松保护和公开您的 API,从而扩大市场范围并提供更好的用户体验。
对于应用和系统
只需轻按一下开关,即可轻松促进 API 与非交互式外部客户端以及内部 API 之间的安全通信。
对于企业开发者
使第三方应用服务器、API 和系统后端能够向您的 API 发出经过身份验证的请求,同时始终保持对精细范围和权限的控制。
众多合规认证,保障身份安全

毋庸置疑,客户数据安全性和合规性是大多数公司的首要考虑因素。Authing 在产品中内置了先进的安全性,因此您无需为您的用户和业务安全忧虑。
行业标准协议:通过采用支持 OAuth 和 OpenID Connect 等行业认证标准的身份平台,提高业务运营和执行的一致性和连续性。
合规性和认证:Authing 拥有多项国内国际合规认证,包括国家三级等保、SOC 2、GDPR、ISO 9001、CCPA、PCI、HIPAA 和 FERPA 等,誓要保障每一位用户、每一个业务的安全。
公共和私有云:在 Authing 的公共云、我们的私有云或您的 AWS 环境中托管您的应用。我们高度可用的多租户云服务每天可以处理大量交易。
快速集成 五分钟实现
单点登录、认证授权、权限管理等功能