快速构建多租户,实现分级管理
通过 Authing 多租户能力,我们得以将不同学校的权限进行分离,赋予每个学校独立管理学生账号的能力
中国第一所国立综合性大学
中国重点大学,位列「双一流」、「211工程」、「985工程」
使用产品
多租户
联邦认证
SDK/API




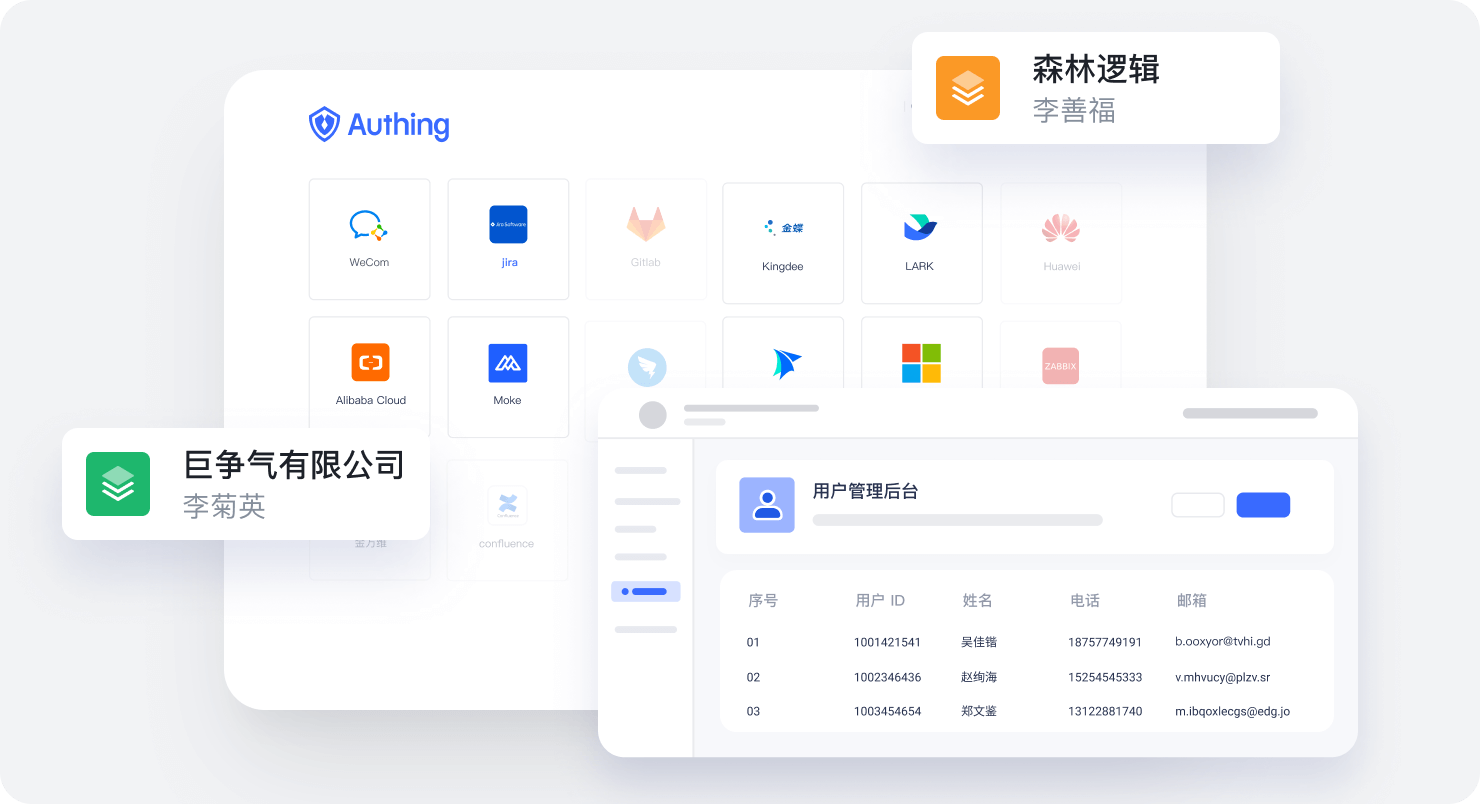
Authing 预集成 2000+ 应用,能帮助企业快速实现单点登录。用户只需登录一次,即可高效安全访问所有应用系统,管理员只需一处即可管理所有用户身份体系,支持企业快速灵活的配置用户登录流程,极大节省企业 IT 人员的工作量,使得企业可以更专注于为客户提供价值的核心业务上。

用户需要访问思政网、大学生在线网、电子教学平台、党建等多个应用时, 需记忆多个账号密码、重复认证,降低了用户登录体验。而且为了方便起见,一些用户可能会采用过于简单的凭据,以便更容易记住,增加了平台数据泄漏风险。
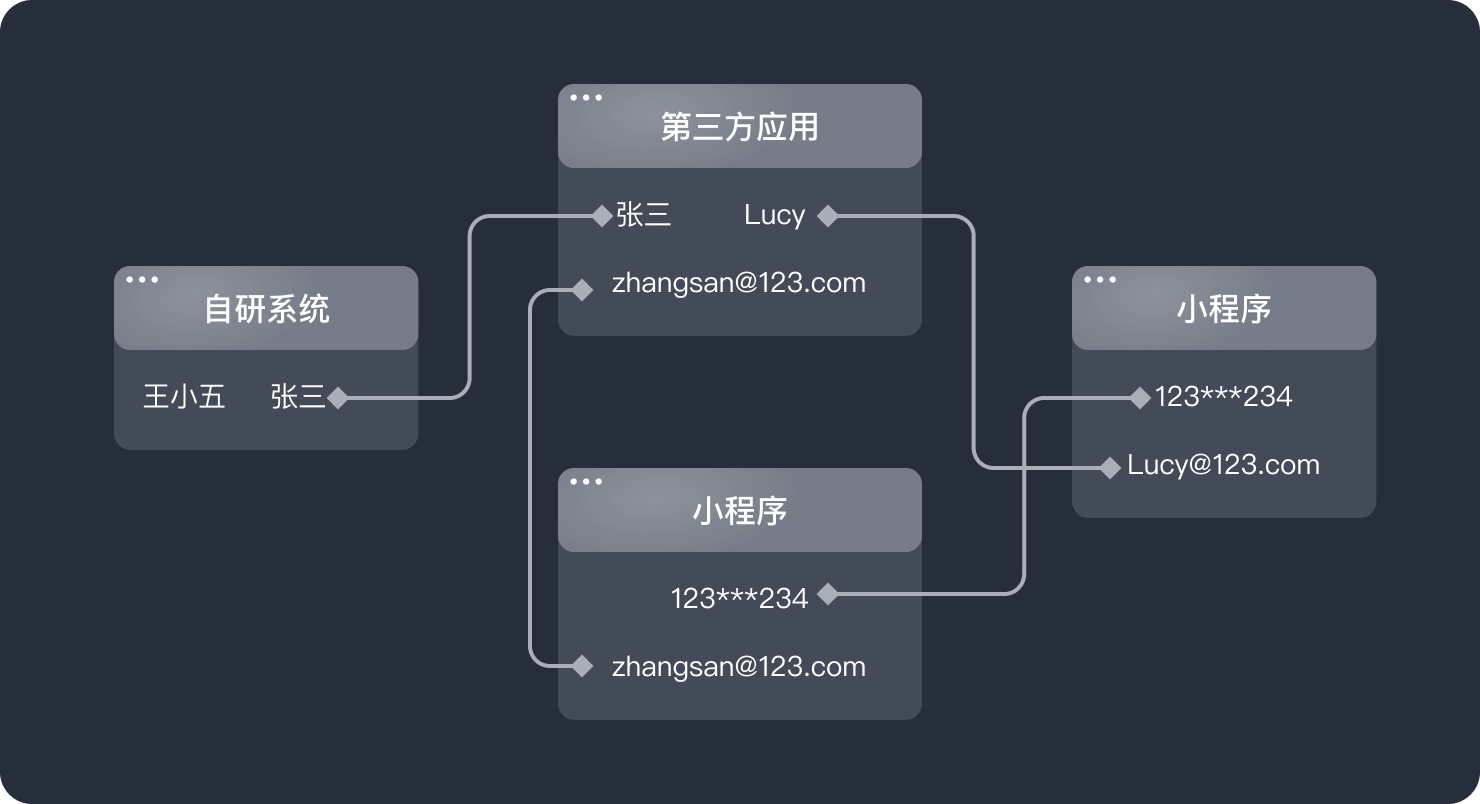
面向终端用户的业务中,唯一用户的合并是刚需,所有的营销和精细化运营都需要建立在 Mapping 后的唯一用户基础上。通过 Authing 快速打通多个应用身份数据,自定义用户合并规则,通过自动化工作流完成条件配置,当条件成立时可以自动化合并用户,并且提供用户管理后台。
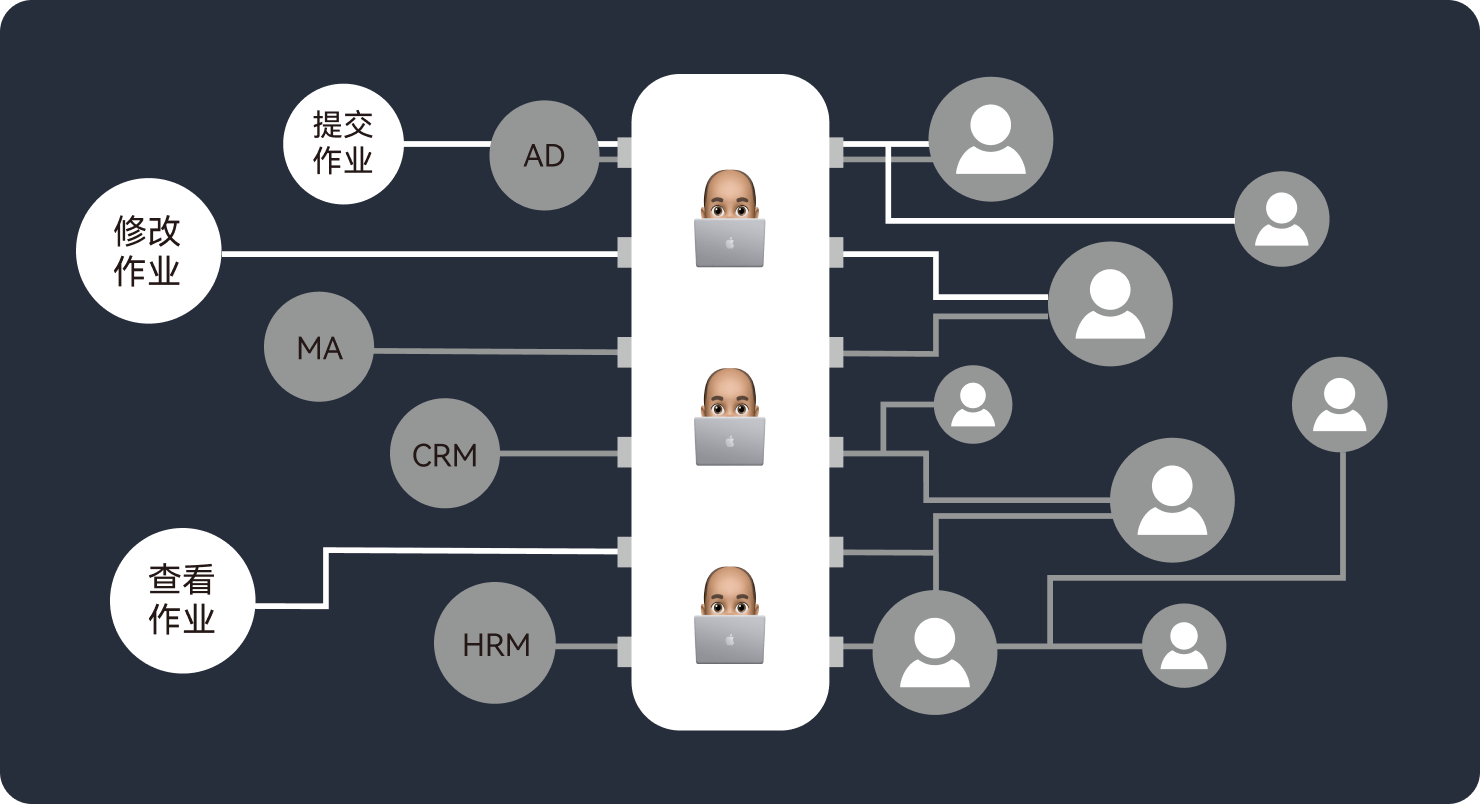
内外部应用平台包含众多数据资源,业务丰富,用户庞杂, 导致 IT 运维和管理工作非常复杂。并且系统内存在多个身份源,系统之间的账号无法一一对应,难以统一管理,大量重复的 IT 运维工作,效率极低。
Authing 支持企业根据自己的需求创建 API、菜单、按钮等资源,定义对应资源操作,以及被赋予权限的主体角色,以用户为单位,提供可视化、全局的权限视图,清晰展示每个用户在不同应用下的资源权限和关联策略,帮助企业管理员轻松查看和管理员工的权限情况, 让教育回归于教育本质。
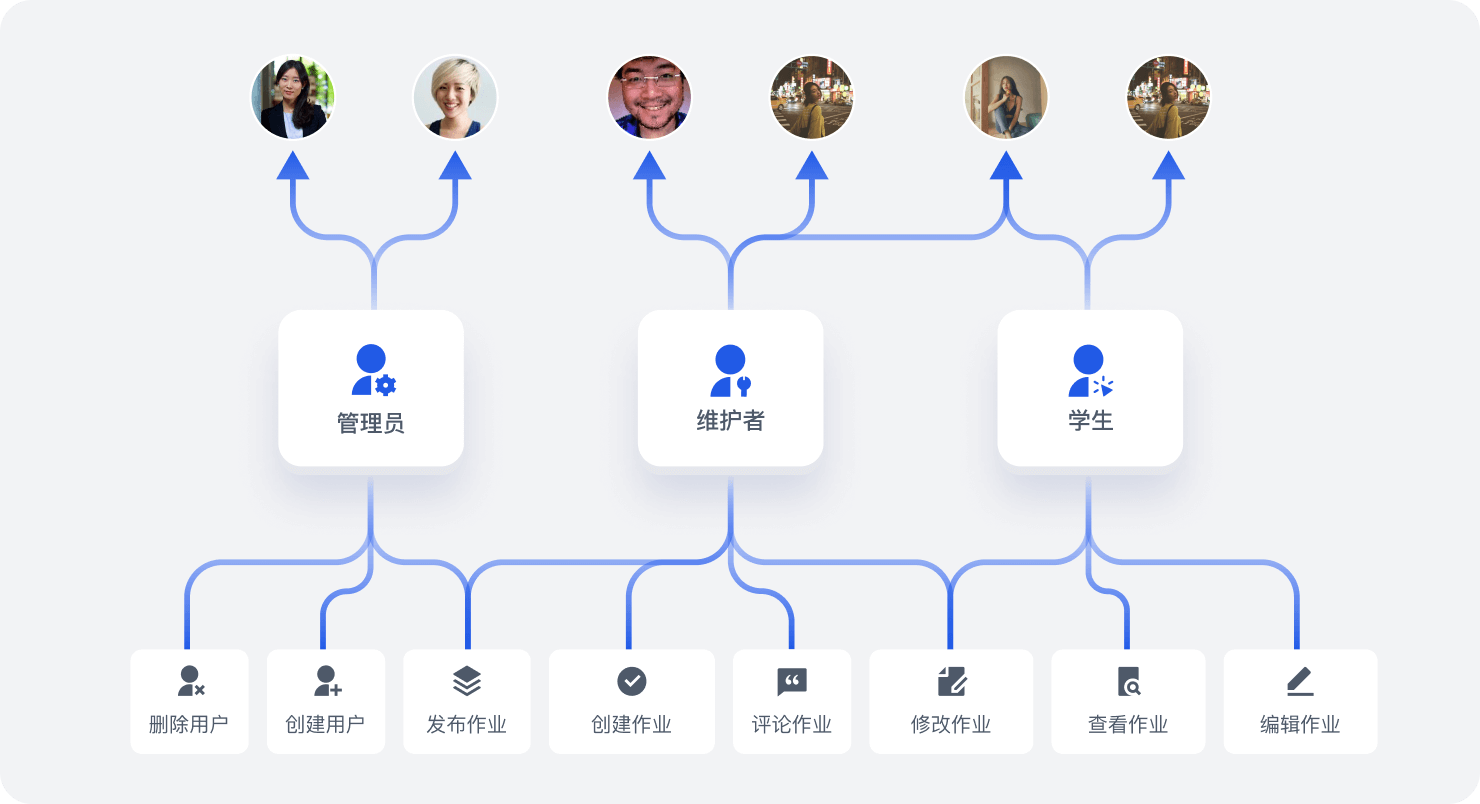
随着企业业务的不断扩展和复杂化,涉及资源共建共享和跨部门协同协作等,用户的角色和资源授权关系复杂且常常发生变化,企业管理员对各个系统的使用情况难以把控,容易造成数据安全隐患。传统权限管理方法无法实现细粒度的权限授予,缺乏统一的权限实体,难以贴合业务现况。