快速集成老旧应用
Authing 帮助我们集成多个新购和老旧应用,缩短了大量的研发时间
世界十大汽车公司之一
日本最大的汽车公司,其汽车销量曾位列世界第一名。
使用产品
应用集成网关
SSO
权限管理
Authing 提供 RBAC、ABAC 等权限管理模型,能帮助企业针对不同场景,建立合适的权限控制策略。开发人员仅需接入 API/SDK,即可高效实现权限管理;还能通过身份自动化能力,动态调整员工访问权限。
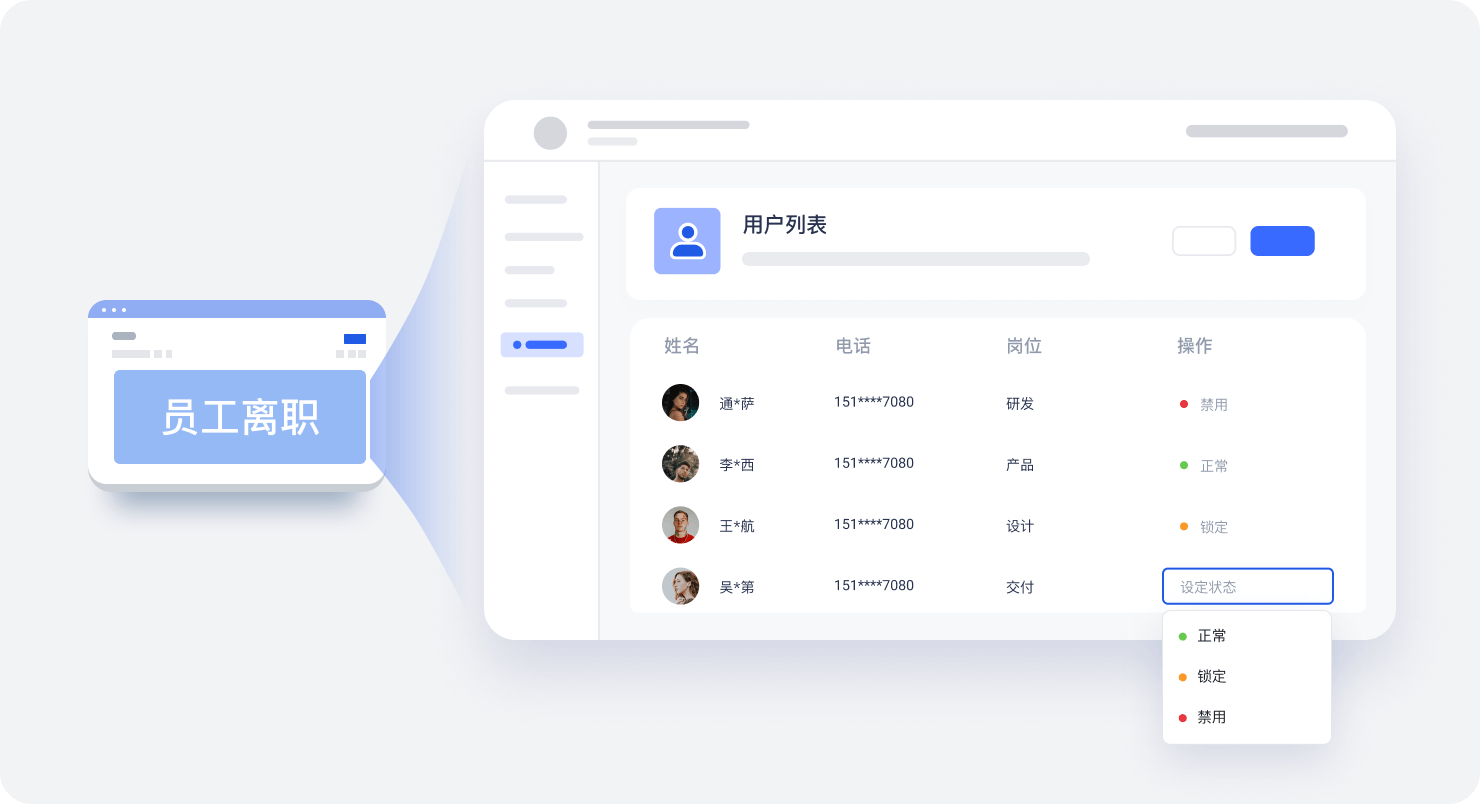
随着新能源造车势力快速发展,行业内人才流动率提升。各业务系统多套并行,权限管理缺乏统一的策略,可能造成关键技术及数据信息的泄漏。然而,权限管理的实现逻辑复杂,自研系统需投入大量研发成本,ROI 较低。
基于 Authing 多租户架构,总公司在统一管理外部供应商、子品牌、下属 4s 店等人员身份的同时,能赋予各供应商/子品牌自行维护本租户内人员的权限,实现各租户数据、权限、设置的独立性。
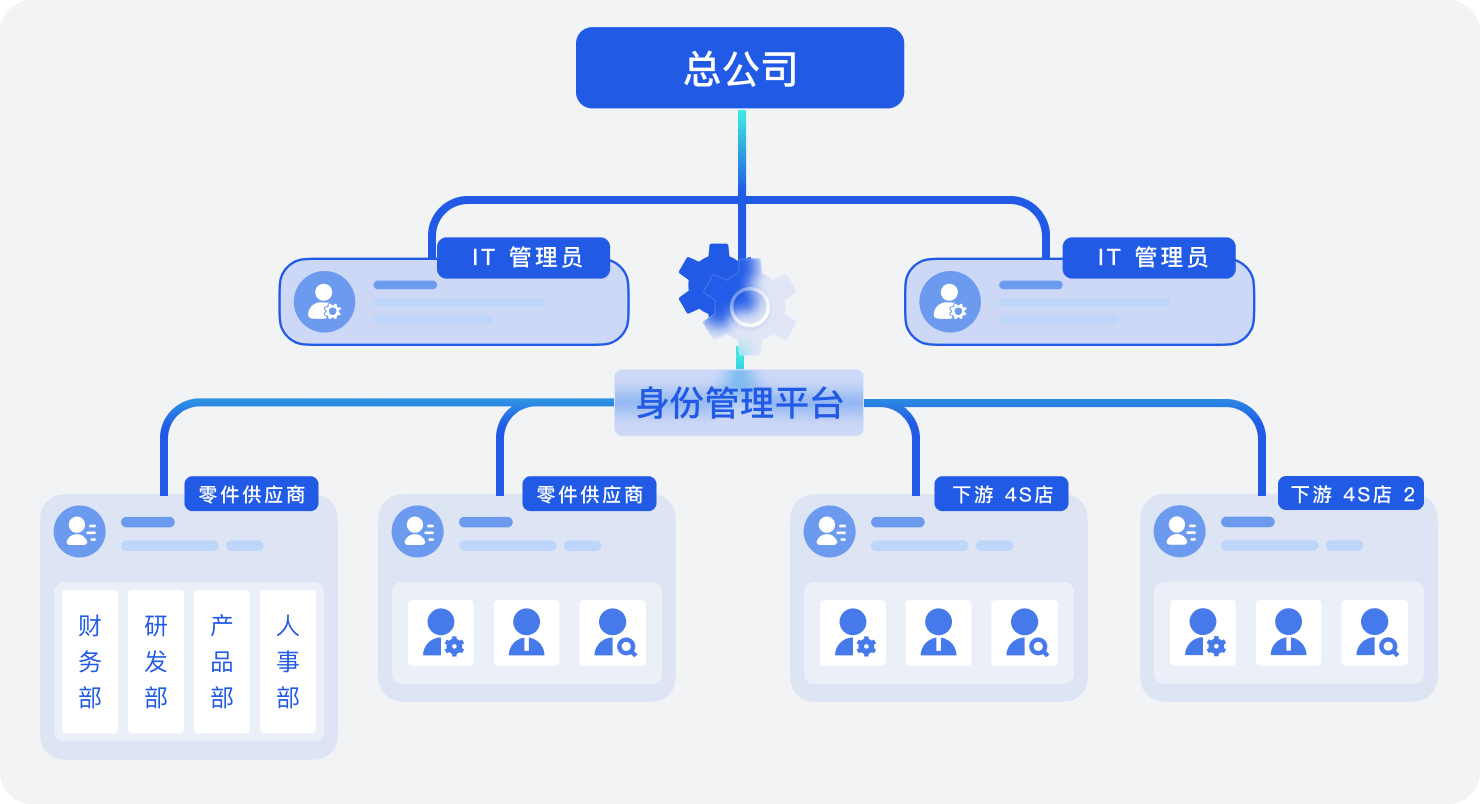
大型车企往往分设多个子品牌,拥有复杂的上下游供应商产业链。各子公司基于自身业务和管理需求独立建设数字化身份体系,各系统数据流通受阻。企业数据需要管理员频繁登录多个系统操作、内部数字传递效率低。
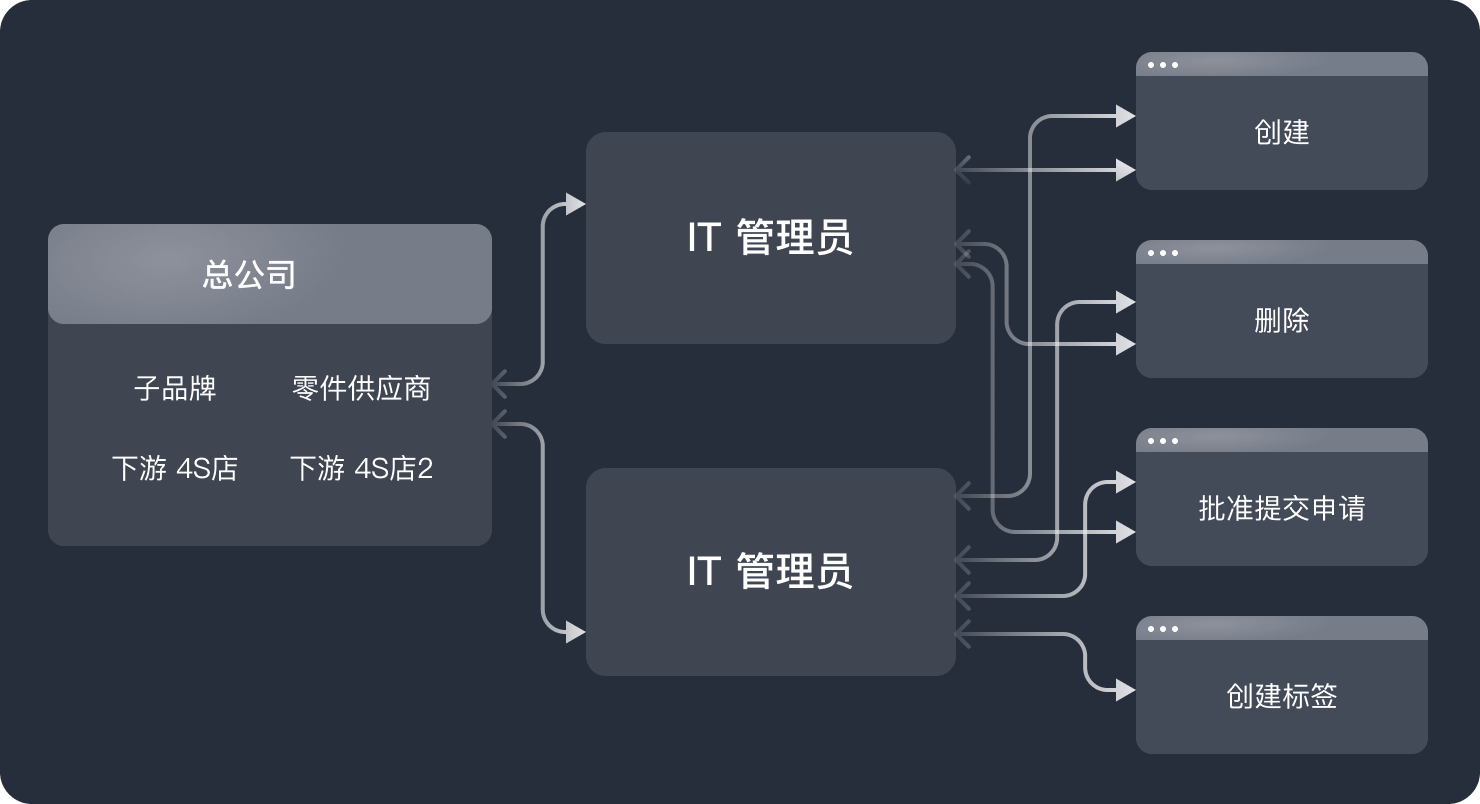
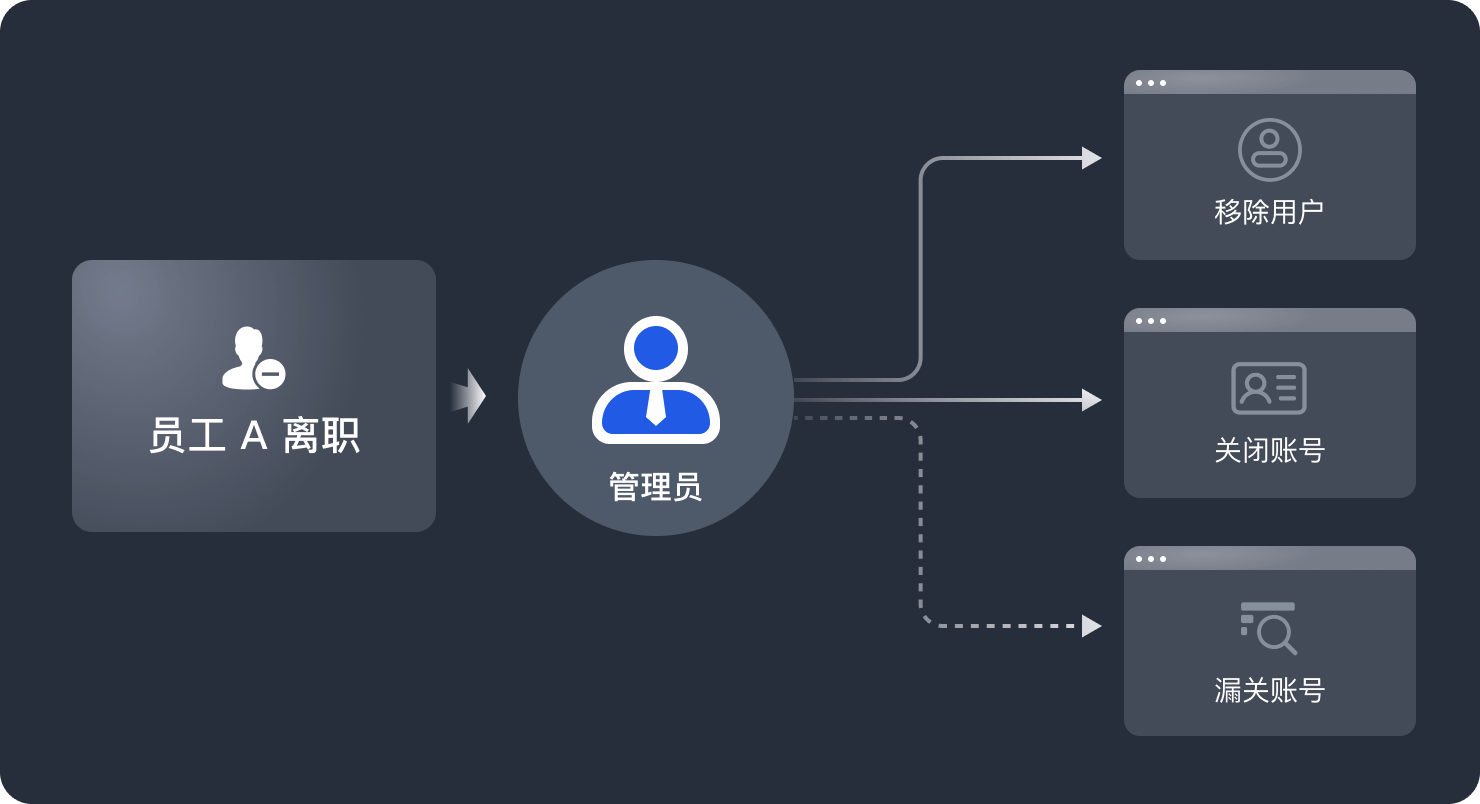
基于 Authing 统一身份认证和身份自动化能力,能帮助车企整合多个系统的身份数据,实现「一处管理身份数据,同步信息至所有应用」,无需手动运维多个系统,一个流程即可及时触发、关闭权限,为不断扩张的汽车制造行业打下数据互通的基础。
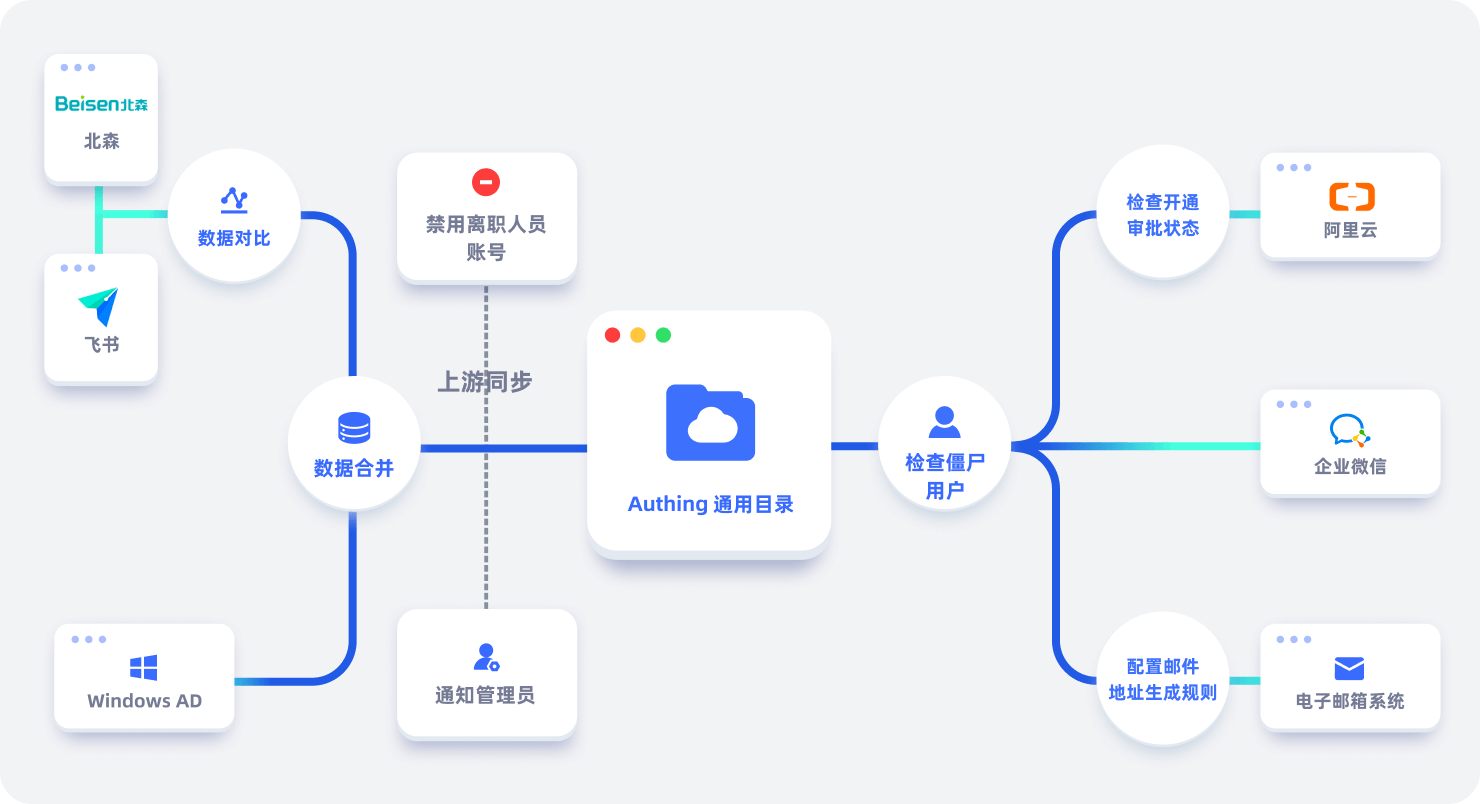
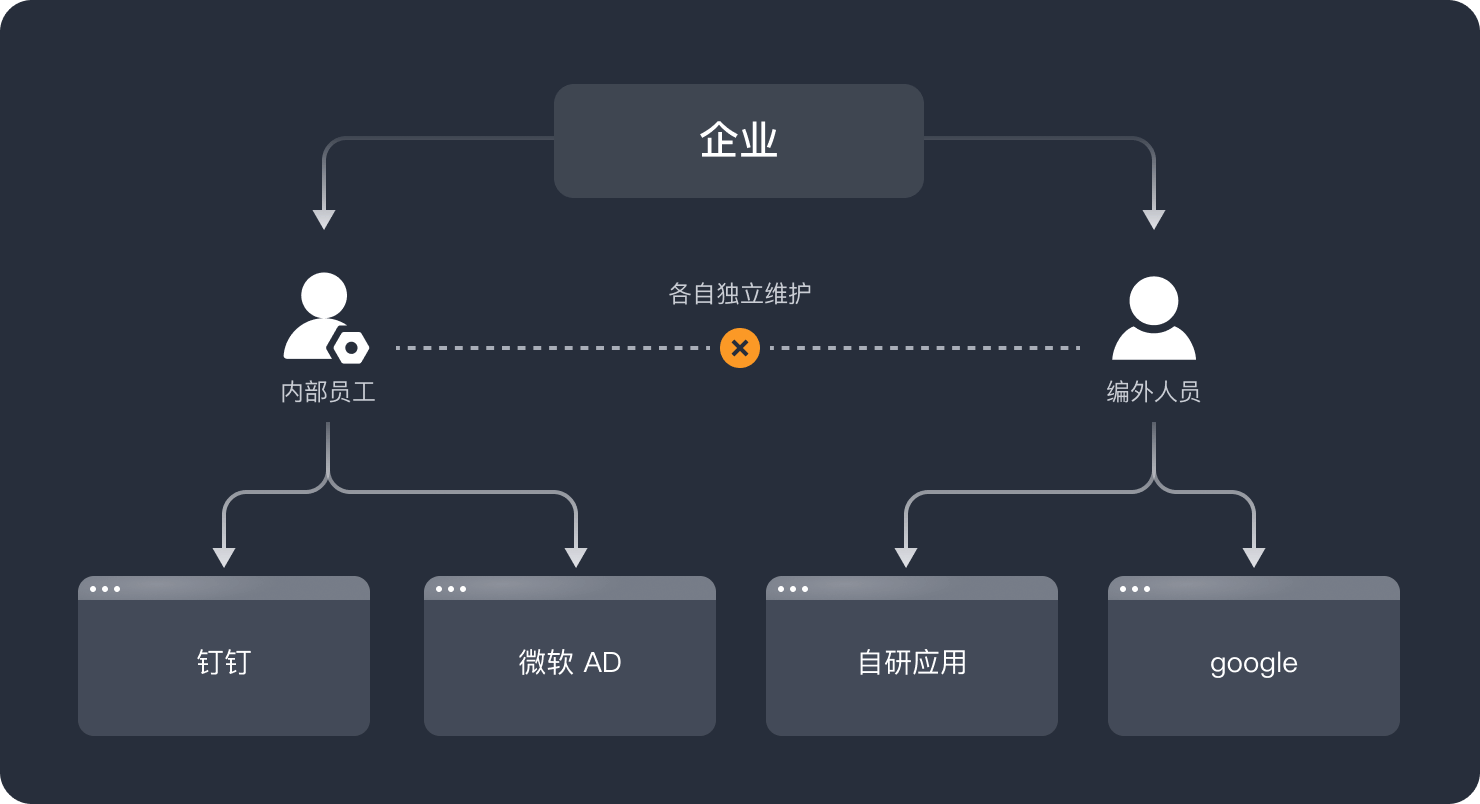
大型车企往往涉及多个业务系统、大量内部员工和编外人员,但不同应用中的人员身份及组织架构数据难以一一对应。使用层面,这导致员工需进行多次认证,操作效率低;管理层面,各应用需要分别进行手动运维,无法及时关闭权限,有数据泄漏的风险。